Risk Assessment and Reporting
As Part of our Digital Cyber Platform, there is a 60 question health check that gives us a snapshot of your current security level based on NIST and ASD Frameworks. With these responses we provide a Cyber Risk Dashboard and work on a plan to address any deficiencies and risk areas within your organisation with our Cyber Toolkit.

Awareness Training and Assessment
In the current Cyber Security landscape, we are seeing attackers targeting people more than ever, and at least 95% of all cybersecurity issues can be traced back to human error somewhere in the chain of events.
With Digital o2’s Digital Cyber Platform you can ensure your users know what to do when faced with a real threat by providing them with targeted, and guided education.
The Cyber Digital Security Awareness Training platform empowers your employees to defend your organisation with a tailored approach resulting in considerably fewer clicks on real-world malicious links.

Phishing Email Campaigns
Digital o2’s Cyber Security Platform allows you to schedule and plan your Phishing campaigns 12 months in advance.
With our integration to Microsoft 365 to auto enroll new staff members, our Platform allows you to simplify and automate your staff cyber training.
Should a learner fail the phishing test, they will be auto enrolled into appropriate additional training programs.

Multi Factor Authentication
What is it?
Multi-factor authentication (MFA) is a security measure that requires two or more proofs of identity to grant you access.
How does it work?
Multi-factor authentication typically requires a combination of something the user knows (pin, secret question), something you have (card, token) or something you are (fingerprint or other biometric).
Businesses as well as individuals should implement MFA wherever possible to better provide security over your accounts, systems, and Identity. Some of the more common MFA options include and offer varying degrees of Security:
- Authenticator app
- Physical token
- Random pin
- Biometrics / fingerprint
- SMS
Why you should Implement MFA?
MFA offers significantly more security and protection against having your accounts compromised than traditional Username and Password Security.
Secure DNS
Secure DNS is the protection of the DNS (Domain Name System) from cyberattacks to keep your Website, Email and other Online Services running and Accessible to your team.
We apply Security solutions with overlapping defences to your DNS Infrastructure and redundant DNS Servers.

Managed Firewalls
There are a now several Managed Firewall Solutions on the market, either in the form of Cloud Hosted, Virtual Appliances or the Traditional Physical Appliances.
These devices Control and Interrogate internet Traffic passing through the device, based on rules and other configured services within the device itself.
A Firewall Device is not designed to be installed in the traditional Plug and Play Environment but is configured and tailored for each individual Network (client) to ensure each firewall’s protection is maximised in each installation.
One of the most important but often overlooked roles of a firewall is the logging and reporting component, we have our own Logging Infrastructure to receive and collate logs for all our managed Firewalls. Our clients get weekly Executive reports with data from these logs.

End Point Protection and Monitoring

Password Management
A password manager is an application often cloud based that securely stores, generates, and manages passwords for all your accounts.
With a password manager, you only need to remember one master password, the password manager takes care of the rest.
Think of a password manager as a safe for your passwords and the master password as the key to the safe.

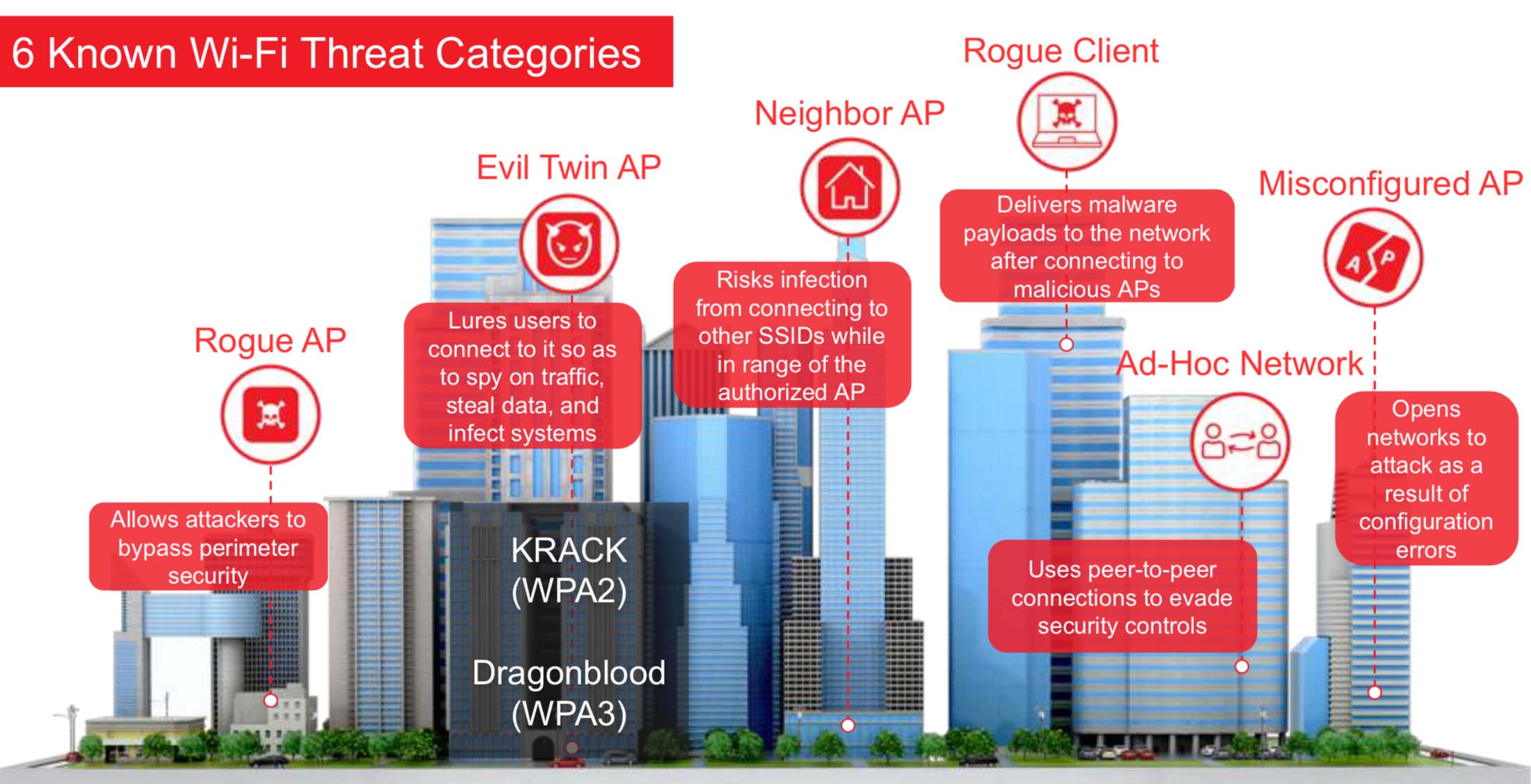
Secure Wi-Fi
Monitor Network activity across your Wireless Network with Active alerts and reporting to ensure your wireless network is secure at all times.